MatchProduct
Graphic Access Tabular Entry [ GATE ], an interception-proof authentication system
Brief Description
Weak passwords make systems vulnerable, yet strong passwords make you forget. Is there a way to keep the passwords simple and yet still make the system strong and secure ?! Yes, there is ! 21st century technology is finally sophisticated enough to fix the weaknesses of traditional passwords. Introducing a digital security innovation : Graphic Access Tabular Entry [ GATE ]. The patented GATE system overcomes all the weaknesses of traditional passwords. It exponentially increase password strength by mixing user pins with other symbols.
Product Details
In modern society, daily life requires the use of a wide variety of information devices, such as mobile phones, PCs, notebooks, and ATMs to name a few. The information devices often keep users' personal data. Due to the importance of protecting this personal data, there are methods to securely lock and unlock these devices.
At present, the most commonly used method to lock and unlock these devices is a password-based challenge authentication procedure, whereby a device typically requires that, before accessing its services, users enter a user id and a password for identity recognition. This is known as a login. This login process is designed to prevent users' personal data from being stolen or fraudulently changed.
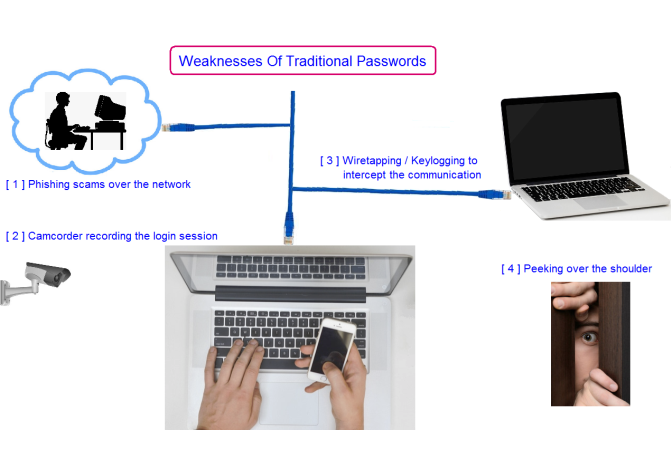
With the rapid daily increase of network coverage and accessibility, hackers are more likely to target users' passwords to gain access to their private information. In addition, hackers are becoming more and more sophisticated in guessing and cracking users' passwords. Therefore, simple passwords no longer provide adequate protection from cyber threats and espionage.
In view of this, various mechanisms have been implemented to provide better protection. For example, users are required to create a password that meets the requirements of password length, complexity, and unpredictability, such that the strength of the password is, in theory, sufficient enough to fend off brute-force search attacks and dictionary attacks.
However, each organization may have a different set of password rules. Some require the password length to be at least 6 or 8 characters. Some require the use of mixed uppercase and lowercase letters, as well as numbers. Some require at least one special character, yet some do not allow special characters. When you think you have just created a very strong golden password (which you can use in all places), you will soon discover that your golden password is invalid in places with a different set of requirements.
As a result of these different password rules, it may be difficult, if not impossible, for users to remember the multitude of passwords they have set up with different sites/organizations. Thus, users will typically store their passwords in a file that is stored on their information device and/or in a password storage application that runs on their information device. The stored passwords can be targeted by hackers, and if they gain access to the device on which the passwords are stored, they will gain access to all the passwords and have access to all of the user's password protected accounts/sites. Therefore, implementing strict rules for passwords to avoid passwords that are too weak can have the opposite of the intended effect (an increased risk of exposing more information).
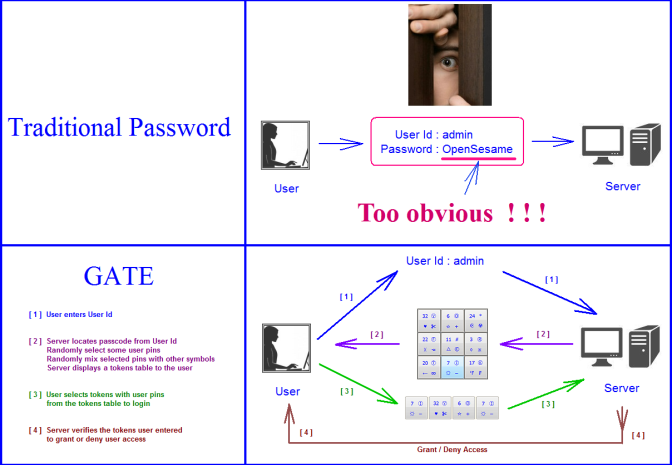
The intention of this invention is to prevent passcode [ similar to traditional password, but can include symbols ] from being intercepted during the process of entering and transmitting. With the protection of the invention, user will not be afraid of being watched by a hacker while entering the information, because the hacker will not know the passcode. Even after many times of observing/intercepting the user entering the login info, the hacker will still remain unable to figure out the passcode.
Introducing The GATE [ Graphic Access Tabular Entry ] System
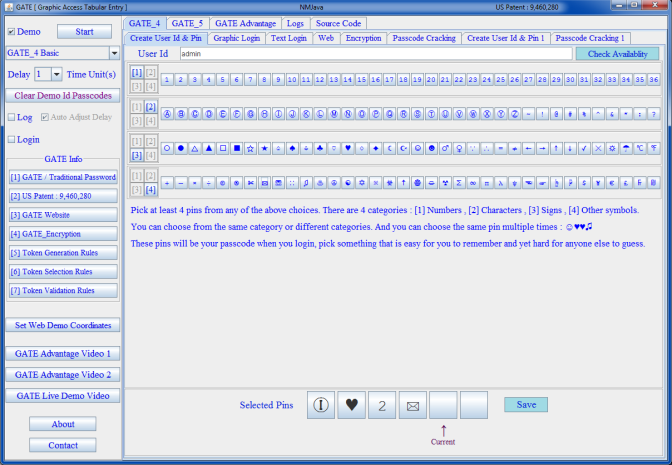
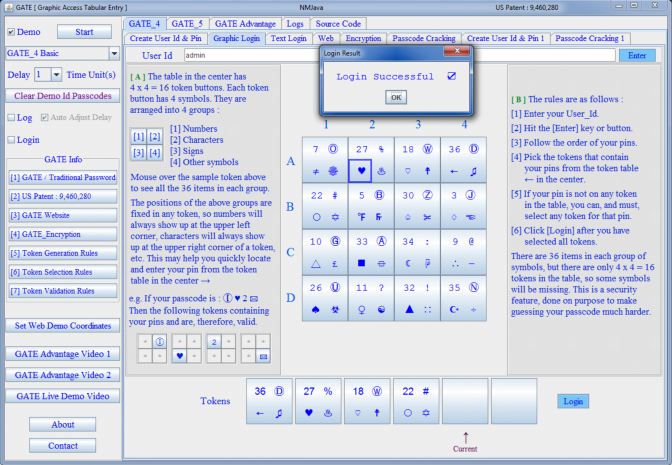
The newly patented GATE system overcomes all of the above weaknesses. Special characters are part of the GATE design. It uses tokens to let user enter user pins from passcode, each token has several symbols, some randomly selected user pins are included in these tokens. It is impossible to tell which symbols in the tokens are valid user pins, which are non-user pins. thereby increasing password strength exponentially. Some user pins might not even appear in the tokens, in that case user can and must enter random tokens in place of those pins, and this uncertainty makes guessing your passcode much harder.
Product Selling Benefits
The GATE system overcomes the following weaknesses of traditional password system :
[1] Too weak ?
[2] Too short ?
[3] Need to add special characters ?
[4] Prone to peeking / interception ?
[5] Prone to phishing ?
[6] Prone to dictionary attack ?
[7] Too many restrictions that you can't even remember your own password ?
[8] Prone to wiretapping
[9] Prone to keylogging
GATE is easy to implement, easy to use, doesn't require any special hardware, nothing physical to carry or to lose.
Each login session is different, so even if someone intercepts a few login sessions, he still won't know what the passcode is.
The GATE system can be used in a variety of devices/places : PC, Cell phone, ATM, door access, online login access, weapons systems, airplanes, ships, safe boxes ... any where that needs access control can use GATE.
Products Specs
| Seller Objective: | Open to discussing any type of sales arrangement |
| Patent / IP Status: | Utility patent issued |
| Inventory in Stock: | In stock and available for sale |
| Number of Units in Stock: | 1000+ |
| Suggested Retail Price: | $300.00 |
| Wholesale Price: | N/A |
| Estimated Cost/Unit: | N/A |
| Minimum Order/Units: | N/A |
| Prior Sales Activity: | N/A |